Nowadays, carrying out daily business operations online has become a norm for many companies. So, there is a rise in demand for dedicated servers for data safety. But, most are under the illusion that their websites are safe. The reason is they think online data can’t be hacked in a premium dedicated server. However, this is not the case. Even the powerful dedicated servers are vulnerable to cyber-breach and cyber-crime.
Importance of Securing Online Data from Hackers
Some reasons for securing your company’s online data from hackers are:
1. Preventing Cybercrime and Fraud: Hackers can steal sensitive personal information such as customer details. This includes their email IDs, phone numbers and credit card details. It results in reputational damage, financial loss and legal complications. So, Tokyo dedicated server or any location’s dedicated server helps you by providing security measures. These include software security updates, firewalls, encryption and DDoS protection.
2. Protection of Critical Data: The loss of critical data due to malware leads to major losses for your company. Small businesses may not recover their data if hacked due to weak infrastructure. So, dedicated server network security keeps your data safe from external malware invasion.
3. Prevention of Data Breaches: A cyber-attack results in a data breach. This gives a huge blow to a business, incurring financial losses. It leads to loss of customers and uncertainty in continuing your business.
4. Prevent Unauthorized Access: Server network security is important for preventing unauthorized access to your business information. It helps in maintaining your data privacy and strong market reputation. Our Amsterdam dedicated server or any location’s dedicated server gives you total control over your server settings.
5. Financial Security: If hackers gain access to your bank account details, they will conduct unauthorized transactions. Also, they will encrypt your key data and ask for ransom. So, you need to focus on securing your website to prevent monetary loss.
6. Complying with Legal And Regulatory Requirements: Many countries have data protection laws that mandate securing a client’s personal information. If you do not comply with the laws, your company has to pay hefty fines. Also, your country’s government may restrict your business operations.
7. Reducing Business Disruption Risk: A cyber attack can affect your daily business operations. This causes daily productivity loss and downtime. So, securing your critical data using a dedicated server ensures the running of your daily business without disruption. It also enhances trust among your clients.
Steps Necessary for Securing Your Website
As a business owner, your priority should be to set up high safety measures. That is to preserve your brand name, brand value, and website data from theft by cybercriminals. It is advised that you remain in touch with our server hosting providers and set the necessary security measures.
Below are the steps you should take to secure your websites:
1. You Should Install All Updates Regularly: Many people skip notifications regarding the installation of the required computer updates. We usually don’t give much attention thinking of unnecessary time wastage. We must remember to install the updates when they arrive. If we don’t, we give an indirect opportunity to cybercriminals to take advantage. These hackers scan and track hundreds of websites every single day to find a lucky chance. If that’s yours, then your business data is at risk.
To avoid such unexpected situations, we advise you to keep an eye on the updates. Also, get your software up-to-date as soon as you can. You should never postpone this. Also, check if there are new security patches available or not. If they are, get them to increase safety. One of the most exploited areas is websites with outdated software. You should try Europe dedicated server or any other location’s dedicated server. This is in case of inability to keep up with the tasks.
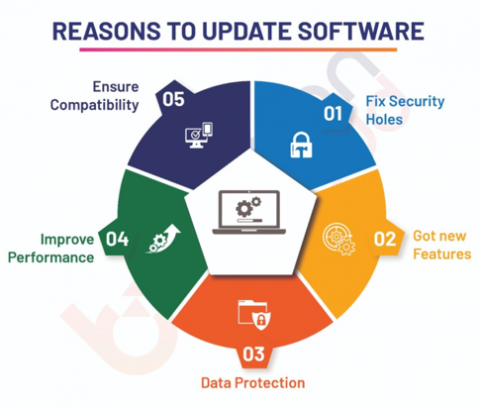
2. Install Software That You Need: You must install only the software that you need. There is a chance of forgetting to check its updates and installing them in case of unnecessary software. It will again make your website vulnerable to attacks from cybercriminals as discussed above.
You should be cautious in case you are a WordPress user. All the free themes that you install, most of them are of no use. This creates the same issues. We forget to check on those themes and plugins regularly. Another thing you should keep in mind is to install software programs only from trusted sources. Also, you must install a firewall to block malicious traffic from reaching your website. This assists in Asia dedicated server or other location’s server security.
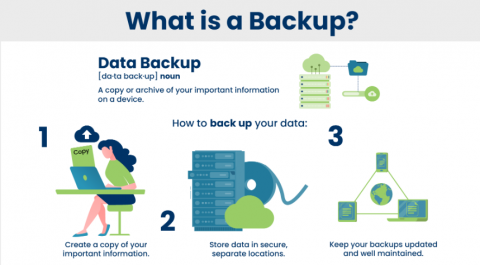
3. Always Backup Your Data: You must have a backup of all the necessary documents and contents. It is very important despite your security measures. It helps in data loss protection in case you are outsmarted by malicious attackers. If that happens, all of your data will be lost. If you haven’t created a backup, your business will be hit hard. You have to recreate all the lost blog posts and videos. You again have to find your confidential documents. This will have a negative impact on your business. Moreover, the reputation of your business will be compromised. So, backing up data on a dedicated server helps in downtime minimization of your tasks.
To avoid all such situations and mishappenings, get a cloud server to back up all your data regularly. This will allow you to restore all the data swifter if it is lost. Thus, your business website doesn’t have to be offline for long. Backups can be both on and off-site. You should create multiple backups to have better peace of mind.
4. You Should Always Use Trusted Networks: This is yet another important checkpoint. Be aware of what’s trusted and what’s not. Your website is susceptible to breaches if you or someone else logs in with a public network. Lay down the necessary security measures to protect something like that from happening. We suggest is to never sign in to your server using a public or a non-trusted network. In this case, a dedicated server is safer for your data privacy. The reason is it provides a private network for carrying out your business operations. Also, changing the login credentials on time increases the level of security even more.
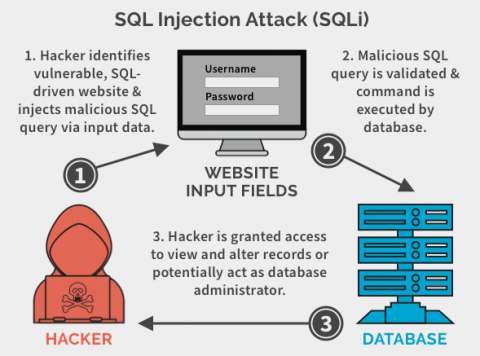
5. You Should Maintain And Secure Your Databases: Cybercriminals love databases where possibly your customers’ valuable financial information is stored. For this reason, securing your databases should be your topmost priority. A breach in your customer’s information will lead to trust issues and your brand value might be negatively affected. You must ensure that your databases are SQL injection resistant. It is crucial to your database security. If you search online, you will find several database administrative tools that you can use. Again, getting a trustworthy and reputable tool is important to avoid any malicious attack. Though our dedicated servers are secure enough for your data protection, your responsibility is also essential.
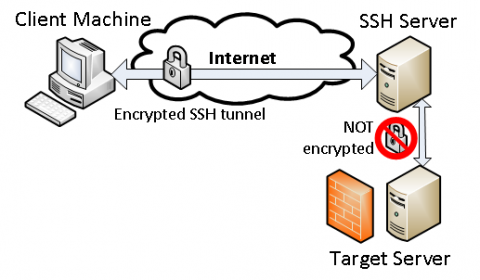
6. Have Secure SSH And Remote Access: Altering the SSH port is an important step. Disabling the root login will make it less vulnerable to security breaches. Also, you need to restrict certain IP addresses that may be harmful. You can also use SSH keys as an alternative to passwords. Further, an SSL certificate helps in data encryption between your website and users. This prevents cybercriminals from intruding on your Paris dedicated server or any other location and stealing information.
7. Never Forget to Get the Right Protection: You should contact your hosting provider and choose a dedicated server type that has built-in protection. As a business owner, you must provide optimal security to your website. Hosting Ultraso provides DDoS protection. Only the best dedicated hosting providers issue this type of protection. You check the security requirements of your hosting plan. After that, discuss with us the add-on benefits of our dedicated servers.
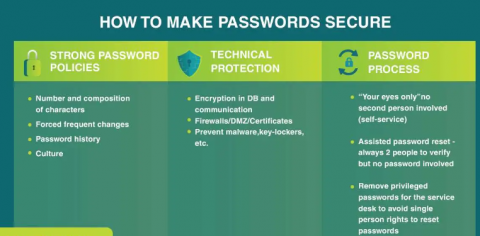
8. Have a Strict Password And Captcha Policy: Always remember to change the password once you get Tokyo dedicated server or any location's server. It may be possible that the service provider has set a default password. It can be vulnerable to attacks. We advise you to change your passwords after a certain interval. Also, design a strong Captcha on forms or website login pages. It prevents automated bots from spamming your website.
9. Don’t Compromise on Regular Testing And Scanning: You find a hosting provider who does regular scans to prevent malicious attacks. You must choose a service provider that offers ongoing vulnerability scans. Also, check your website to see if it shows any unexpected behavior.
10. You Should Establish an Emergency Protocol: Developing an emergency protocol helps you in the long run. In case someone breaches your security measures and accesses your data, having an emergency protocol will create less panic. You can execute certain preset steps to minimize the loss. An emergency protocol will include the following. First of all, set up a point of contact at your company’s data center. This creates a situation about how a security breach can impact your customers. After that, designate a system with an admin lead to help in case of emergencies. The above are the steps that are included in an emergency protocol. You should take your time and take care of these steps. It benefits in securing your Amsterdam dedicated server or any location's server from cyber-attacks.
Everyone wants security. Your customers trust you with their personal information. A security breach or data loss creates a distrust that affects your business in the long run. So, you as business owners should take the right steps and implement the right measures. These are essential in avoiding hazardous consequences.
Summary
It is a wrong perception that premium dedicated servers 100 % protect your business data. Some steps from your end are essential to secure your data from hackers. The points in discussing the importance of securing data from hackers are written. It is essential for protecting your business’ critical information. It also assists in protecting your customer’s data. After that, some ways of protecting your data from cyber fraud are discussed. First, you must install your updates whenever there is a notification. Second, you must keep your software up-to-date. It provides less chance for hackers to intrude into your system. Third, you must have a backup of your important documents. This will make you less worried in case a hacker succeeds. Also, choose a dedicated server that provides DDoS protection. Hosting Ultraso has many server types that have multiple protection features. At last, change your dedicated server password every few months for database security. So, after purchasing our dedicated server, follow the above steps for cyber-security.
Closing Thoughts
As more companies are shifting to online business, data security is becoming an issue. So, businessmen must focus on their data protection apart from depending on a dedicated server. The above points will provide you with ideas on how to take extra caution on data protection.
Blog Category:
- Abhik's blog
- Log in or register to post comments



